Encryption
Protects DataEncryption Protects Data
Deniable
Protects
You
Encryption Protects DataDeniable Protects You

The only OS designed to withstand coercion. Unlock your device—expose nothing.
Your Security Is Only as Strong as Your Ability to Withstand Coercion.
Encryption protects your data—until someone forces you to unlock your phone. In high-risk environments, standard mobile security isn't enough.

The Only Mobile OS With True Coercion Resistance
Protect your data even when physically compromised. No other mobile OS offers this level of security.
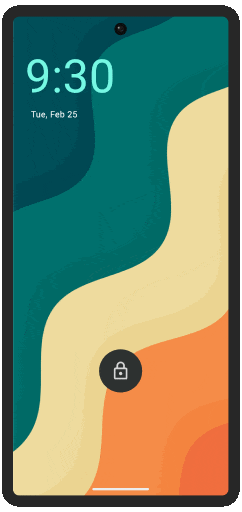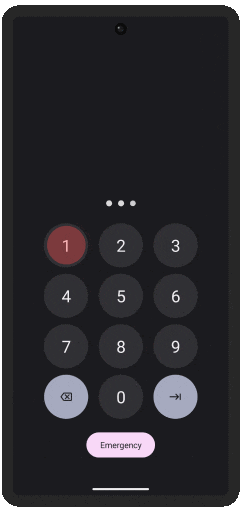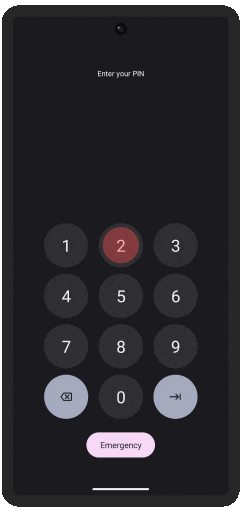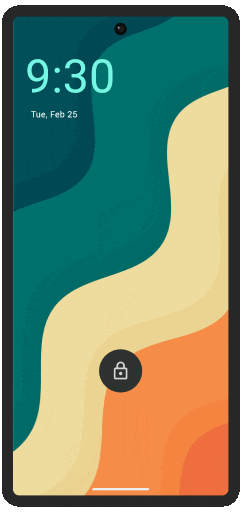
Two OS, One Device
Even the strongest encryption fails when someone has physical access. That's why we built two completely separate environments—a normal OS for daily use, and a hidden one for sensitive data.
Seamless Switching at Unlock
One password reveals your everyday Public OS that appears completely normal—even under forensic analysis. Another unlocks your invisible Secure OS, which can be instantly erased if needed.
Forensic-Proof Encryption
Even advanced forensic tools can't detect the hidden OS. No partitions, hidden folders, or metadata—just a normal Android phone on the surface.
Trusted Tools, Ready to Use
Preloaded with Signal, Telegram, ProtonMail, and Tuta—no extra setup required. Secure communication, right out of the box.
Trusted by Organizations Facing Real Risks
Journalists & Investigative Reporters
Safely carry critical information through dangerous environments without exposing sources.
Private Security & Intelligence Teams
Prevent unauthorized access to mission-critical data when operating in hostile regions.
Oil & Gas Professionals
Carry devices safely in regions where digital espionage and intrusive inspections are common.
NGOs & Humanitarian Workers
Secure sensitive field reports and evidence, even under forced inspections.
Deploy It Your Way: Software or Pre-Installed Devices
Deniable OS is a software-only security platform. Unlike other secure phones, it doesn't rely on specialized hardware or factory-installed modifications.
Software-Only License
For organizations with IT teams that need maximum control and security. Install in the field on locally purchased or company-owned devices.
- Install securely in the field—no need for pre-shipped hardware
- No risk of supply chain tampering—use any locally purchased device
- Deploy via simple web installer—no complex setup required
Pre-Installed Devices
For teams that need immediate deployment without IT overhead. Receive ready-to-use devices with Deniable OS pre-installed.
- Ready to use immediately—pre-configured with Deniable OS
- Discrete, secure shipping—no external markings or branding
- Best for organizations without IT teams or those needing fast deployment
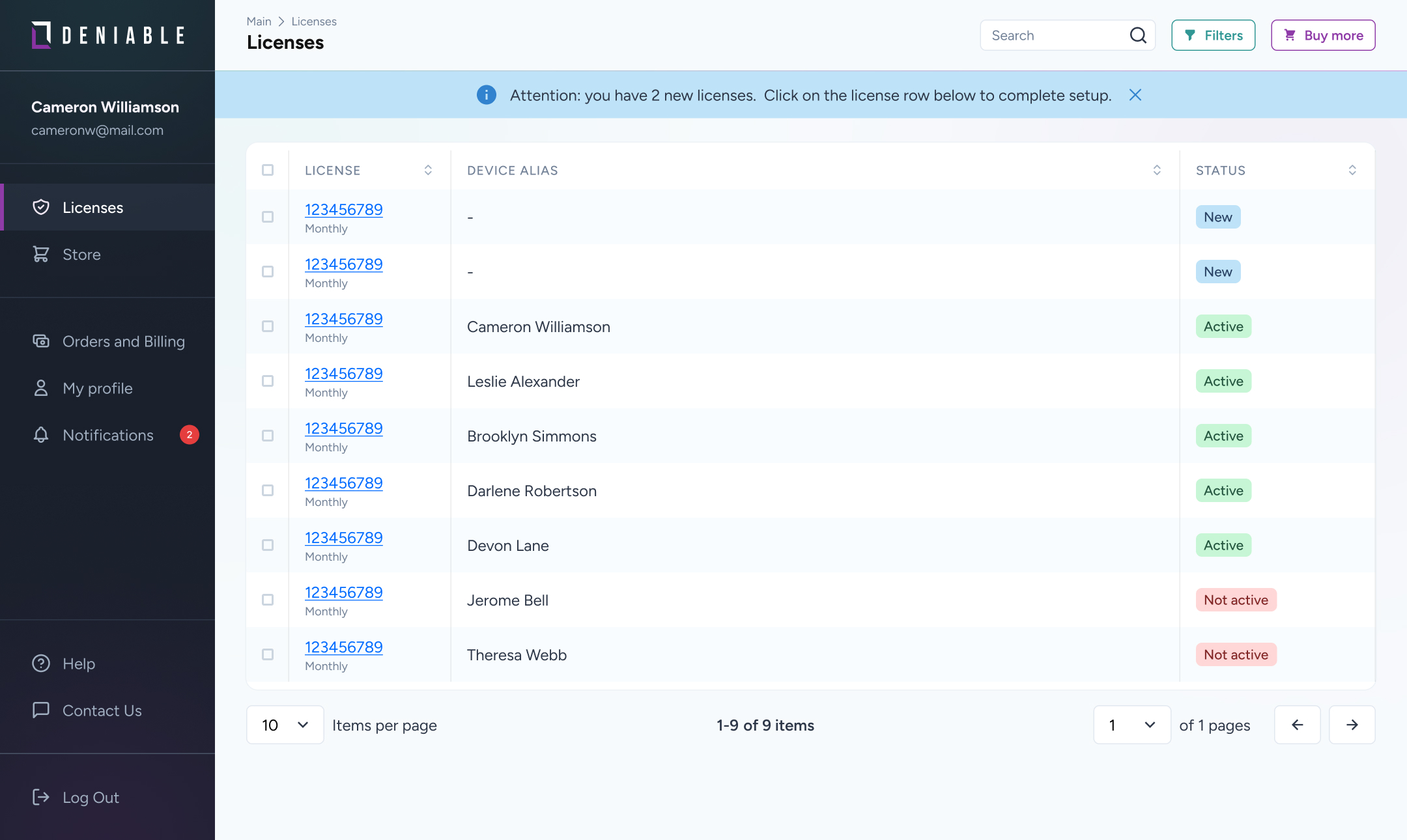
Manage Your Secure Devices with the Deniable Web Dashboard
Security doesn't stop at the device level—organizations need control. The Deniable Web Dashboard gives teams a simple, powerful way to deploy, manage, and revoke devices—all without compromising security.
License Management
Issue & revoke licenses—ensure only authorized devices run Deniable OS
Remote Security
Remotely revoke access if a phone is lost or compromised—disable it instantly
Scale Deployment
Deploy at scale—easily activate and track hundreds or thousands of devices
Simple Updates
Install OS updates in the field—no IT expertise required
Zero Trace
No central point of failure—the dashboard leaves no trace on the device itself
Team Control
Perfect for both large teams managing security at scale and small teams ensuring seamless onboarding

With a Deniable phone, I feel safer knowing that even if I'm stopped and searched, they won't find anything."
DR, journalist, Denmark
When I use a Deniable phone in public, it looks and feels like any other device—no one can tell the difference."
VS, journalist, Ukraine
Staying unnoticed is critical for us. Deniable helps us operate without drawing any attention."
KM, NGO manager, Liberia
I know that even if authorities check my device, they won't find anything sensitive when I have this operating system."
GH, democracy activist, Cambodia